Table of Contents:
As a SaaS offering, the NetSuite service includes a robust set of features to provide security and protect your company - and your company’s data, like data encryption and infrastructure security via OCI data centers.
In addition to the features that work behind the scenes, and don’t require you to do anything to leverage them, NetSuite also offers tools that you can leverage, with good processes, to improve the overall security of your NetSuite instance and your company’s data.
Here are some suggestions for how to leverage these tools.
Request More Info About NetSuite Security Tips and Tricks
NetSuite Security Tips and Tricks
Managing User Access For Better NetSuite Data Security
Employees leave. Passwords get stolen. In the worst case, employees sometimes abuse their access to your systems out of greed or anger (i.e. they become an insider threat).
In any of these cases, the user who needs access to NetSuite can become a threat to your system’s security and bypass many of the measures put in place to protect your data. Fortunately, there are measures you can take to protect against these threats.
User Roles
User roles are central to security in NetSuite, as they limit the potential damage from compromised logins and insider threats. There are some principles to follow when creating and assigning user roles to make them effective for security and internal controls.
Permissions should be granted - and user roles chosen - based on the principle of least privilege. This means that roles should be created with the lowest level of permissions a user will need to do their job, and permissions should only be increased or added when the current permissions are found to interfere with the user’s ability to perform their duties.
When a role is selected for a user, it should be a role that only gives them access to the records, fields, etc they need to complete their work. Finally, it means that administrator roles should be reserved for account administration tasks and never assigned or used for user tasks.
Along with the principle of least privilege, roles and users with more responsibility and broader access across the organization should be given less - not more - permissions. This helps to mitigate the risk inherent in these users having the broad access and authority required for their work.
Segregation of Duties
Segregation of duties is distributing a process across multiple people (i.e. multiple users in NetSuite) to limit the ability of an individual to act alone.
Ideally, this means preventing any single user from carrying out an end-to-end process, like procure to pay. As an example, if the same user isn’t able to create or edit a vendor and enter or pay a vendor bill, it becomes much more challenging for someone to use the system to send money from the company to themself.
Small teams can often still achieve good segregation of duties by creatively spreading duties across different functions. If you only have one AP clerk and one AR clerk, for example, you can have the AP clerk manage customer records and the AR clerk manage vendor records.
Managing Users
It is important to establish - and follow - clear processes for user management, including for provisioning access for new users, assigning roles to users, and removing access when a user no longer needs it.
These processes should be auditable - unfortunately, this means email-based processes are not recommended - to protect against privileged users abusing the ability to provision users and add roles.
The offboarding process for employee departures should include an action item for removing access - not just to NetSuite, but to all company systems.
Finally, there should be a process for reviewing who has access, what roles they have, and if they still need the access and roles assigned to them. “Orphaned” users, who no longer require access (e.g. former employees) but were never removed, are a major vulnerability and should be removed as part of this periodic review.
Monitoring Your NetSuite Instance For Security Breaches
Even if you take all the right steps, there is a chance that your system can somehow be compromised. If this happens, the key is to identify and stop the threat promptly before more damage can be done. To achieve this, NetSuite’s saved search functionality is a great tool.
Saved searches can be set to email any new results. If you identify actions in the system, like logins from suspicious locations or anomalous transactions, you can use the saved search email functionality to send an alert to key people to investigate.
A timely response to contain a threat is essential, and a proactive alert will help you respond quickly.
In addition to alerts, saved searches can be used to report on access by all or a subset of users. These reports should be reviewed periodically to look for anything suspicious which may have slipped past your alerts.
In particular, administrator logins and activity should be reviewed with an extra level of scrutiny; the all-encompassing access given to an administrator out of necessity makes them inherently higher risk.
Reviewing administrator access with extra scrutiny will also help to ensure the administrator role isn’t being used for regular user activities.
Identify NetSuite Integrations and Scripts Impacting Security
Automation can both help and hinder security. On the one hand, human users can be the biggest vulnerability in NetSuite’s security, so reducing what those users do in the system can reduce the vulnerability they create.
On the other hand, automations may bypass other internal controls, like approvals on journal entries and can multiply the impact of a user’s actions, including one who is a bad actor.
For integrations, other systems may have less robust security than NetSuite, and an integration could introduce vulnerabilities from the other system into NetSuite. If robust authentication isn’t used for the integration, it may be easier for an attacker to gain access to NetSuite through the integration than any other way.

However, data still needs to move between systems, and a “swivel chair” integration means trusting people to follow good practices while interacting between the systems.
Because integrations, scripts, and workflows have the potential to either help or hinder your overall security, they should always be evaluated through a security lens to ensure they are being designed and implemented in a way that will do the former instead of the latter.
Cloud Data Security: A NetSuite Guide
Your Company’s Journey into Cloud Security:
An Infographic Guide on how NetSuite Can Help You Get There
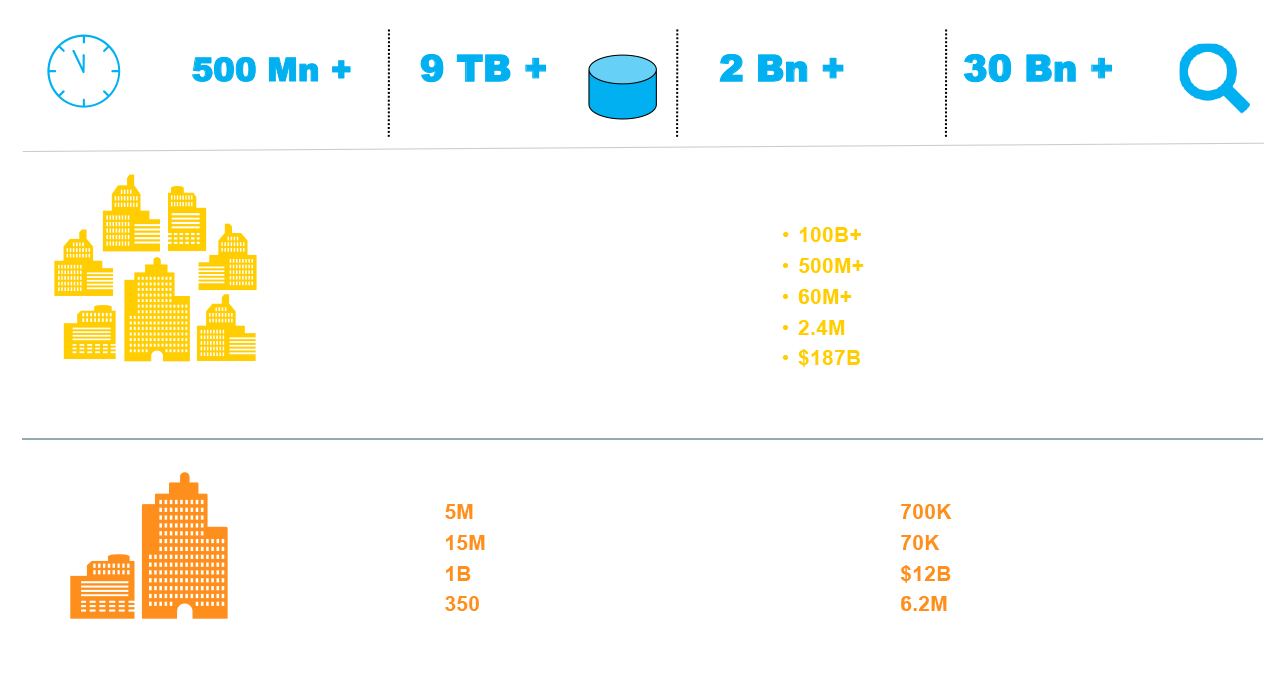
As the cloud industry grows more significant in today’s business market, so does its impact on overall company privacy and security concerns. The cloud-computing market is estimated to reach $912.77 billion in 2025, and grow 21.20% from 2025 to 2034.
So, the question then becomes: How is a rapidly evolving business landscape guaranteed to maintain control over their information in primarily cloud-based infrastructure?
NetSuite ERP is one of the leading enterprises in the cloud industry. Over the years, they’ve leveraged experience with over 40k organizations to come up with the strongest security solutions the market has to offer.
Here’s what you need to know of their roadmap to ultimate digital security:

NetSuite Cybersecurity: Secure At Every Level
Data Center
- Guarded premises
- Managed physical access
- Separation of duties
Network & Host
- Continuous monitoring through multiple intrusion detection systems (IDS)
- Third party scans and penetration tests
- DDOS protection & redundant backbone connections
- Operations Security Team
Database
- No direct access to database
- Real-time replication between data centers
- Opt-in access for services & support
- Three layers of separation between application and data
- One-way hash encryption of sensitive CC data
Application
- Granular roles and permission system
- Per-role authentication requirements
- IP address restriction
- Configurable password policies
- Two-factor authentication
- Single Sign On (SAML v2)
- Full audit log available via built-in reporting

The NetSuite experts at GURUS will leverage NetSuite’s secure designs and cloud infrastructures to help future-proof your growing business. Every feature and safeguard is specifically made for the challenges that today’s companies are facing when it comes to safekeeping their data.
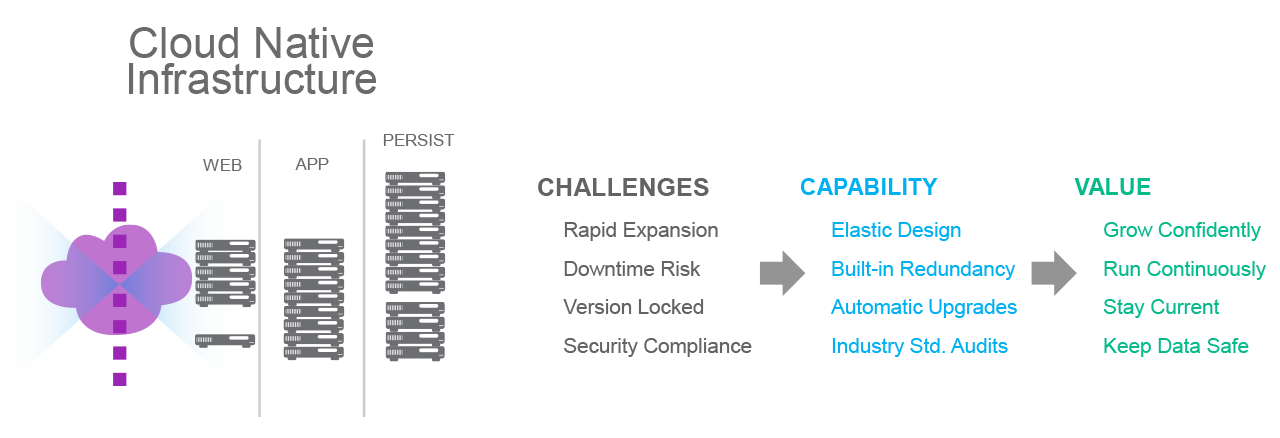
NetSuite’s Cloud Security Advantage: Future Proofed For Scale
Cloud Native Infrastructure:
Learn More about Securing your Cloud Data with NetSuite